I recently upgraded my home network router from a pfSense SG-1100 to a Ubiquiti Unifi Gateway Ultra. The main reason I upgraded was because I already had a unifi switch and unifi wireless access points, and so wanted to complete the eco-system.
ISP limitation
My ISP uses Carrier-Grade NAT or CGN which means it uses a IPv4 network shared with other house-holds. It also means I cannot port forward services like VPNs to the Internet. A static IP address is available but it’s £5 extra a month.
As the title of this blog post suggests, I will be using IPv6 which my ISP also provides.
Unifi console
The MAC Address Clone option is enabled and matches the MAC of my ISP supplied device’s WAN interface. This was the only way I could get both IPv4 and IPv6 addresses to appear in the web console.

- IPv4 - Uses DHCPv4 with CloudFlare’s DNS resolvers
1.1.1.1and1.0.0.1. - IPv6 - Uses DHCPv6 with prefix delegation size
/56(depends on your ISP).
However, I soon found out that this wasn’t enough…
Create a VPN server instance
I’m not going to bore you with how to create a server. But when a new VPN instance is created the server IP address will ALWAYS be the WAN IPv4 address. There is no way to supply a IPv6 address, at least from the new web console interface.
I’ve also noticed the Wireguard VPN server listens on all interfaces. However, when trying to connect to my WAN IPv6 address the handshake never completes. The OpenVPN VPN only listens on the WAN IPv4 interface.
root@UCG-Ultra:/# netstat -luntp | grep -iE '1194|51820'
tcp 0 0 100.xx.xx.xx:1194 0.0.0.0:* LISTEN 725345/openvpn
udp 0 0 0.0.0.0:51820 0.0.0.0:* -
udp6 0 0 :::51820 :::* -
It’s also possible that my ISP is somehow blocking outbound UDP but that’s unlikely.
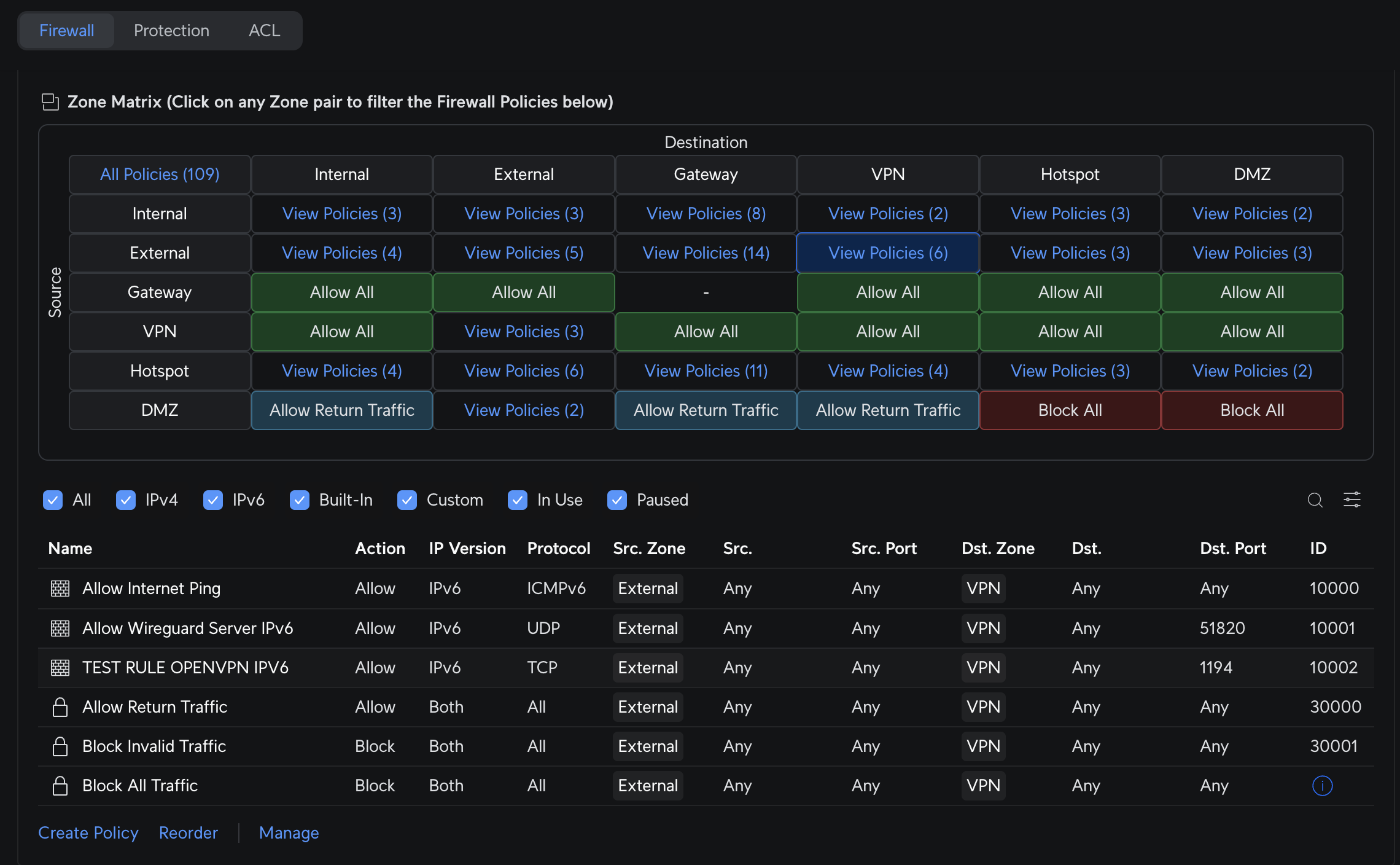
Create Firewall rules
Created two rules rules to allow external traffic on IPv6. Here is a screenshot of the new “Zones” feature for managing firewall rules on Unifi web console. It’s actually pretty neat!

But even after setting these rules I still couldn’t get either OpenVPN or Wireguard to connect.
Using socat to forward IPv6 to IPv4
Yes, we can use socat to forward IPv6 network packets to the CGNAT WAN IPv4 address. There is probably a better way, but this one worked well. Here’s a quick command and options I used:
socat TCP6-LISTEN:6666,reuseaddr,fork TCP4:100.xx.xx.xx:1194
What the options mean:
TCP6-LISTEN:6666- listen on all IPv6 interfaces on TCP port6666reuseaddr- allows an immediate restart of the server processfork- each connection spawns a child new process (do not terminate connection)TCP4:100.XX.XX.XX:1194destination WAN CGNAT IPv4 address for OpenVPN server
If socat doesn’t exist, install it with apt install socat (uses Debian as base OS).
Create a system service
We will also create a new service that will start every time the device reboots. Create a file called /etc/systemd/system/socat-vpn-redirect.service and add the following (update to match your settings):
[Unit]
Description=socat service for OpenVPN server IPv6 to IPv4
After=openvpn.service
Requires=openvpn.service
[Service]
Type=simple
SyslogIdentifier=socat-vpn-redirect
ExecStart=socat -d TCP6-LISTEN:6666,reuseaddr,fork TCP4:100.xx.xx.xx:1194
Restart=always
[Install]
WantedBy=multi-user.target
We also want to make sure the service starts after the OpenVPN service.
To start the service to at every reboot type systemctl enable socat-vpn-redirect, and run the service type systemctl start socat-vpn-redirect. Here’s an example of the service running:
root@UCG-Ultra:/usr# systemctl status socat-vpn-redirect
● socat-vpn-redirect.service - socat service for OpenVPN server IPv6 to IPv4
Loaded: loaded (/etc/systemd/system/socat-vpn-redirect.service; disabled; vendor preset: enabled)
Active: active (running) since Mon 2025-03-03 22:46:11 GMT; 1min 27s ago
Main PID: 2479605 (socat)
Tasks: 1 (limit: 3529)
Memory: 692.0K
CPU: 10ms
CGroup: /system.slice/socat-vpn-redirect.service
└─2479605 socat -d TCP6-LISTEN:6666,reuseaddr,fork TCP4:100.xx.xx.xx:1194
Mar 03 22:46:11 UCG-Ultra systemd[1]: Started socat service for OpenVPN server IPv6 to IPv4.
Mar 03 22:46:11 UCG-Ultra socat-vpn-redirect[2479605]: 2025/03/03 22:46:11 socat[2479605] W ioctl(5, IOCTL_VM_SOCKETS_GET_LOCAL_CID, ...): Inappropriate ioctl for device
root@UCG-Ultra:/usr# netstat -tupan | grep -i 6666
tcp6 0 0 :::6666 :::* LISTEN 2479605/socat
Useful
A couple of links of users experiencing the same issues:
-
Support for IPv6 VPN-Server (WireGuard) (ui.com 2024)
-
WireGuard server connection through ipv6 - help needed (ui.com 2024)
-
Vpn with IPv6 (or IPv4 behind a cgnat) (ui.com 2024)
-
UDP Pro - VPN/IPv6 (reddit 2020)
Summary
It’s 2025 and Ubuniqti are still yet to support basic IPv6 configurations. This short guide may be useful for those who don’t mind using IPv6 for VPN access, and save £5 per month on their ISP bill. Or for those with no choice but using IPv6 to expose services.