This is a short blog post on how you can get root access on a Android 12 emulated device with Google services, using a tool (script) called rootAVD by newbit1. I also share a few recommendations which are helpful during mobile analysis.
Android Studio
For mobile analysis I generally use my Google Pixel 3a device. However, sometimes I will try to avoid it if I can, especially when I’m only curious about an app’s network traffic or API endpoints. I will use the Android Studio device emulator instead.
Android Studio supports three types of system images:
- Google Services and PlayStore
- Google Services
- Open source project (without Google API or PlayStore)
The following screenshot shows an example of different system images available under the device creation configuration pane. You can see there are a various targets, architectures and API versions options:
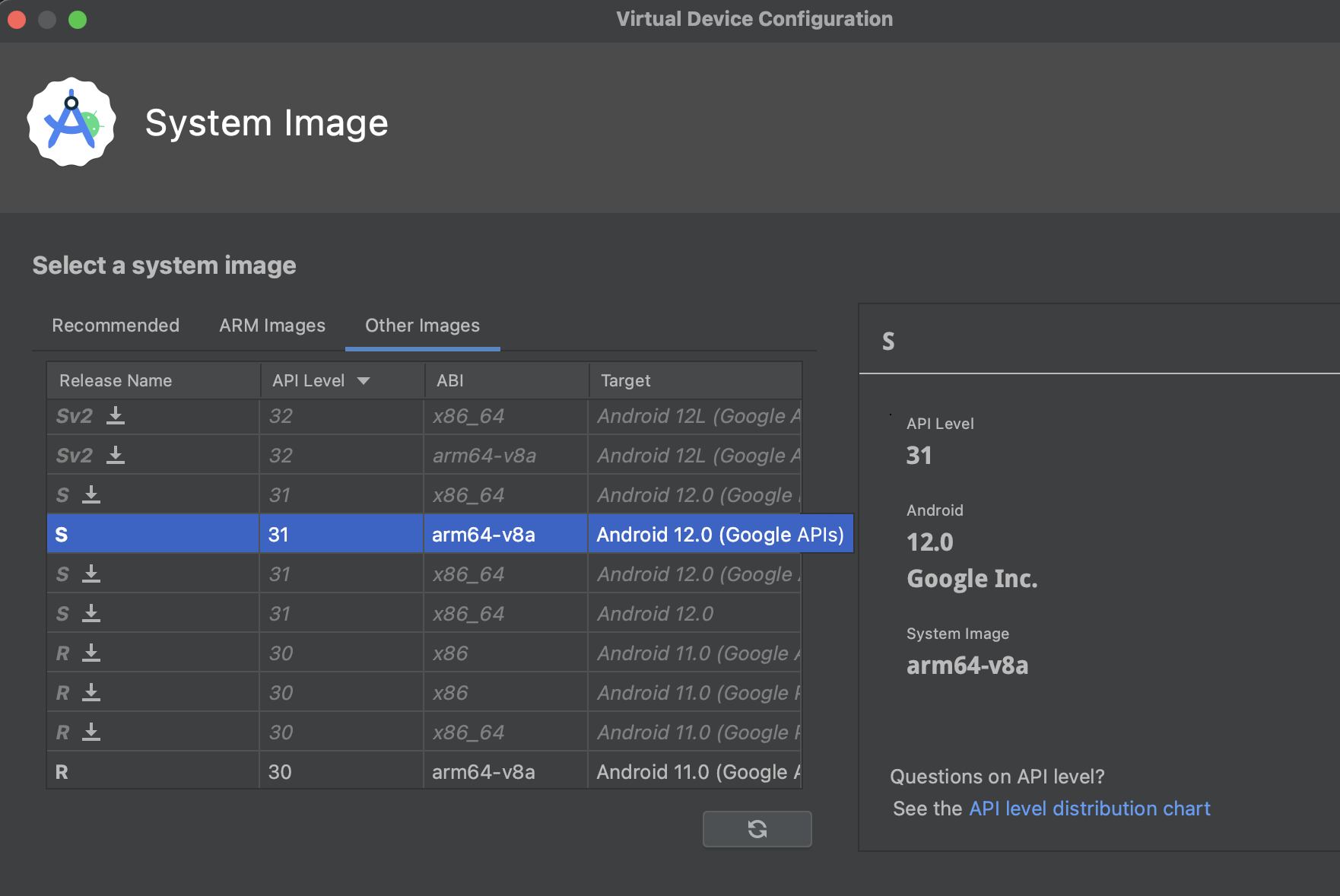
I opt to go for the Android 12 with arm64-v8a image with Google Services PlayStore. This configuration was chosen because I’m running on the Apple M1 chip, and I also want to be able to download apps from the PlayStore.
Note: Not all apps are available from the Play Store on an emulated device.
rootAVD
rootAVD is available on GitHub https://github.com/newbit1/rootAVD. It is a collection of scripts that automatically modify Android Studio Virtual Device system files, in order to gain root using Magisk.
There’s really only three steps:
- Create a AVD on Android Studio
- Show a list of available AVDs and paths:
./rootAVD.sh ListAllAVDs - Select a AVD to be rooted:
./rootAVD.sh ~/Library/Android/sdk/system-images/android-31/google_apis_playstore/arm64-v8a/ramdisk.img
Extras
After successfully rooting a device, I highly recommend doing the following.
Install Magisk Modules
These are some of the modules I use to extend the features of Magisk.
- AlwaysTrustUserCertificates by Jeroen Beckers - move user certs into system store.
- MagiskFrida by ViRb3 - start a Frida server during device boot.
- Universal SafetyNet Fix by kdrag0n - attempt to bypass Google’s SafetyNet features.
Create a Snapshot
When your virtual device has been configured. I suggest creating a snapshot. This is especially helpful when you’re analysing malicious apps, or when you’re doing something dangerous which might corrupt the system.