A short guide on how to block the entire .zip TLD using pfSense. In particular using a package called pfBlocker-NG, which can be thought of as a “PiHole” alternative. pfBlocker-NG is capable of much much more but won’t be covered in this blog.
Why is .zip TLD a problem?
It’s simple really, Phishing. Whether it’s abusing a HTTP URI scheme or using special unicode characters, having a .zip TLD which has always been attributed to the compression file extension is just a bad idea.
Here are some excellent resources explaining the problem in greater detail:
- The Dangers of Google’s .zip TLD - the author mentions a bug reported in Chromium which allow hostnames containing U+2044 (⁄) and U+2215 (∕), which is almost identical to the forward slash (/) in URL PATHs. And can be used to trick users.
- Zip domains, a bad idea nobody asked for - also references the above.
- google-zip-mov-domains-social-engineers-shiny-new-tool - mentions there hasn’t been active abuse (yet).
Install package
Note: It’s now recommended to install the
pfBlockerNGversion rather thanpfBlockerNG-develversion, since both versions have synced up.
On your pfSense admin panel, go to System and Package Manager.
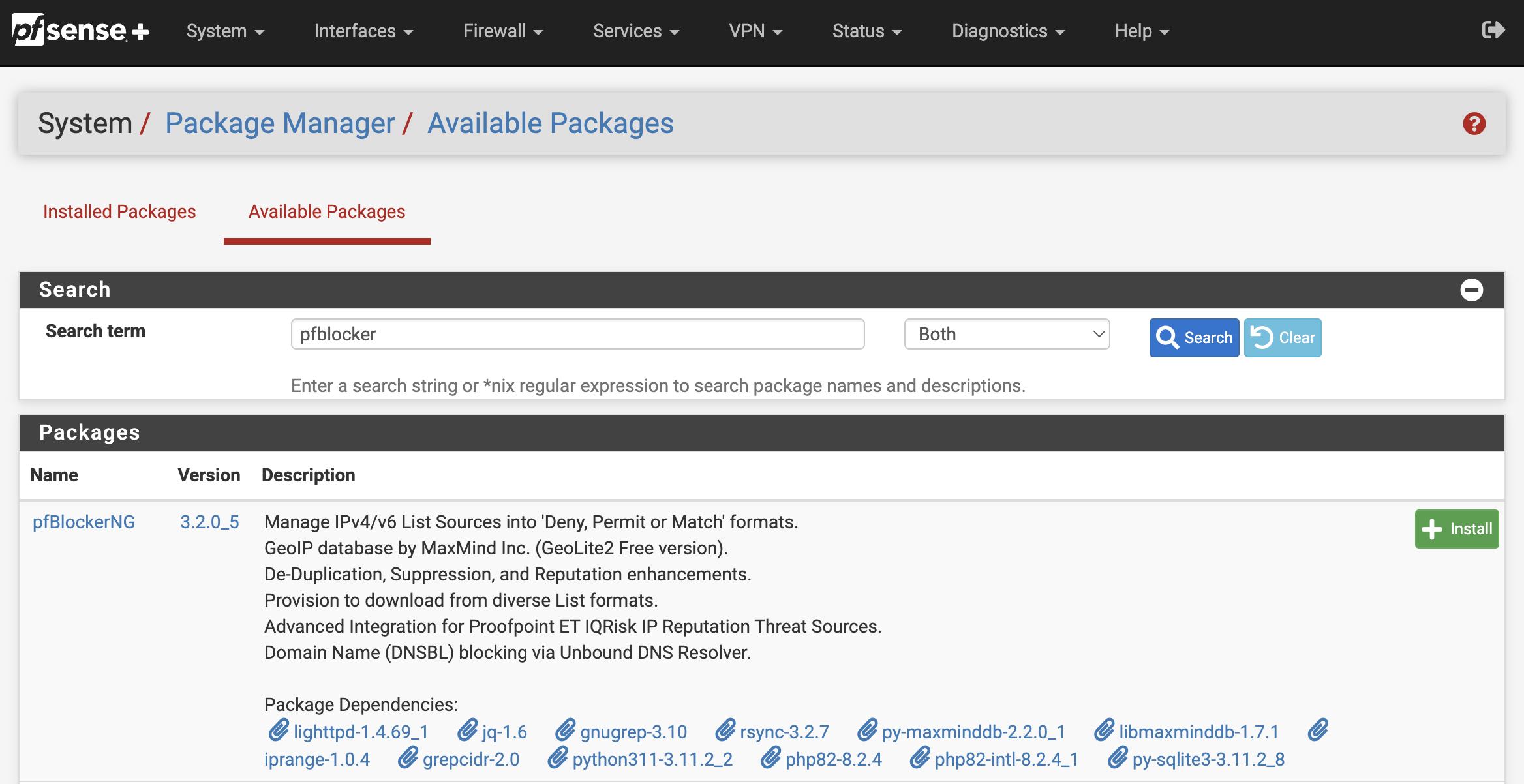
Select Available Packages and make sure it’s the latest then hit Install.
Configure package
A new option will now be available under the Firewall menu called pfBlockerNG.
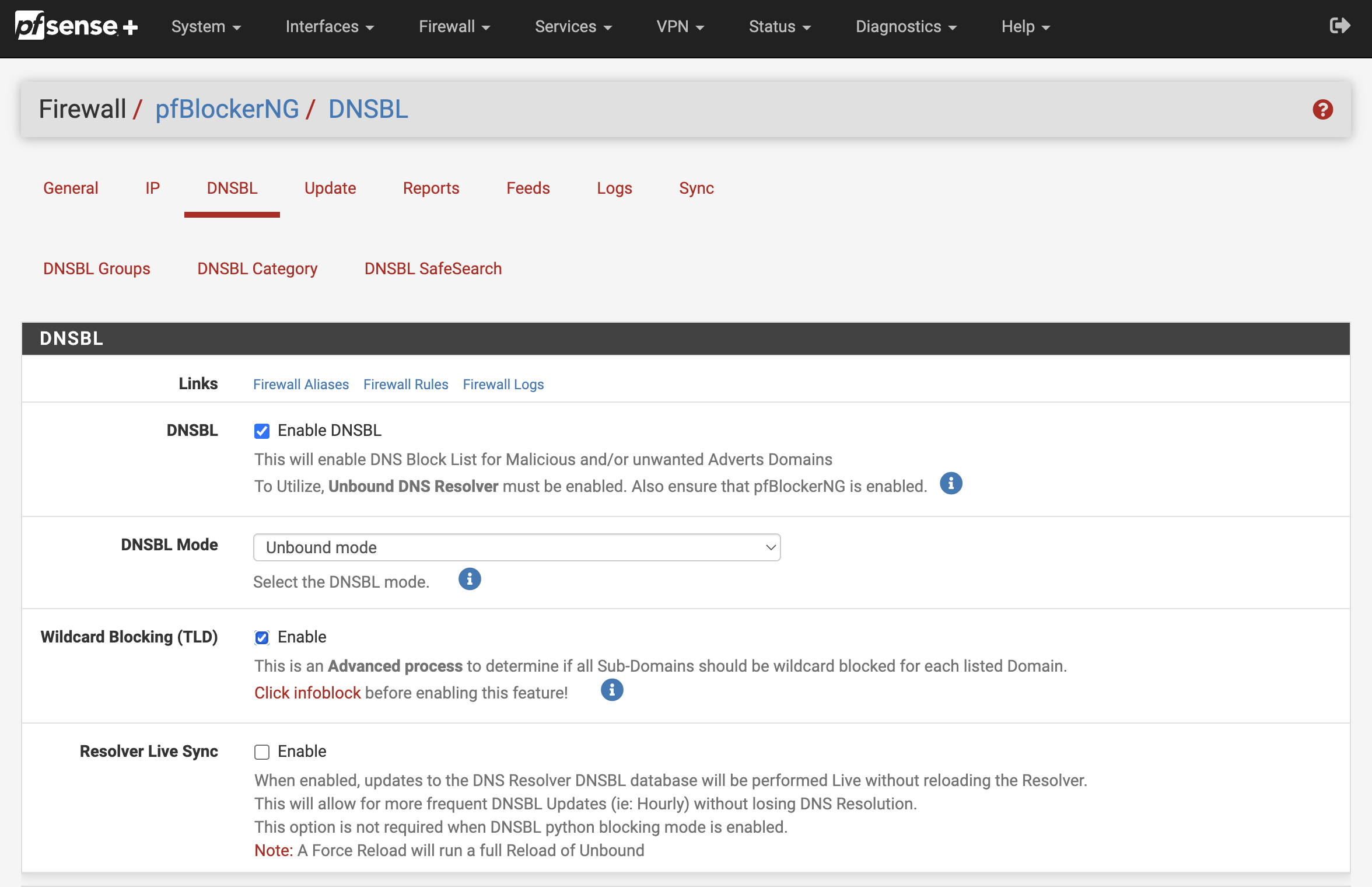
Go to the DNSBL pane and make sure these options are enabled:
Enable DNSBLWildcard Blocking (TLD)
Whilst on the same page scroll down until you see TLD Blacklist/Whitelist and expand it. Next, add your chosen TLD to the TLD Blacklist input field (without the dot). You can block multiple TLDs, but it must be separated one per line e.g.
zip
mov
pw
zw
ke
quest
support
When you’re done click Save DNSBL settings.
The final step is to reload the settings by going to Update (still in the pfBlockerNG menu) and clicking on Reload. If you don’t it’ll update in 1 hour automatically by default.
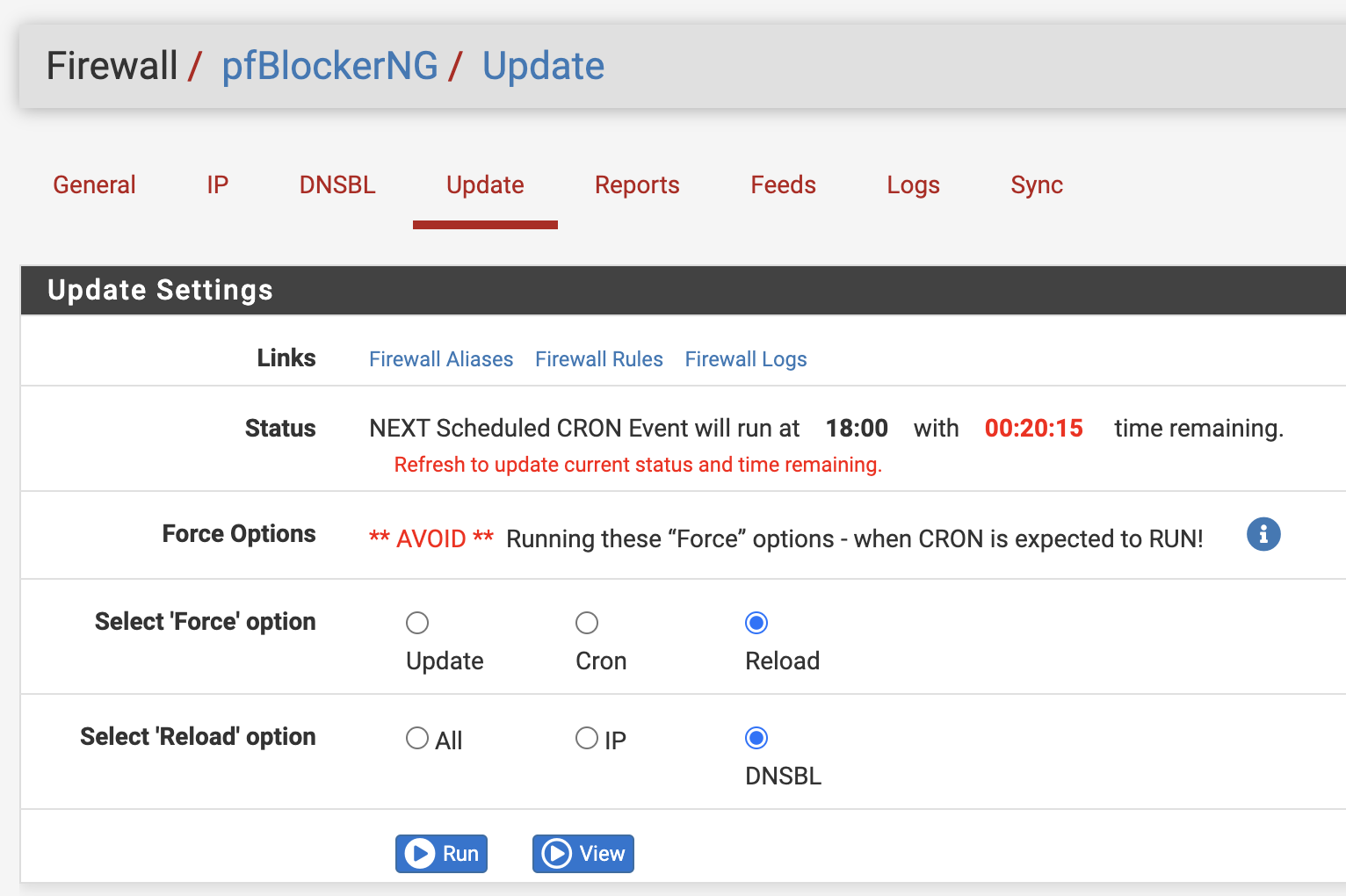
Confirming
Browser
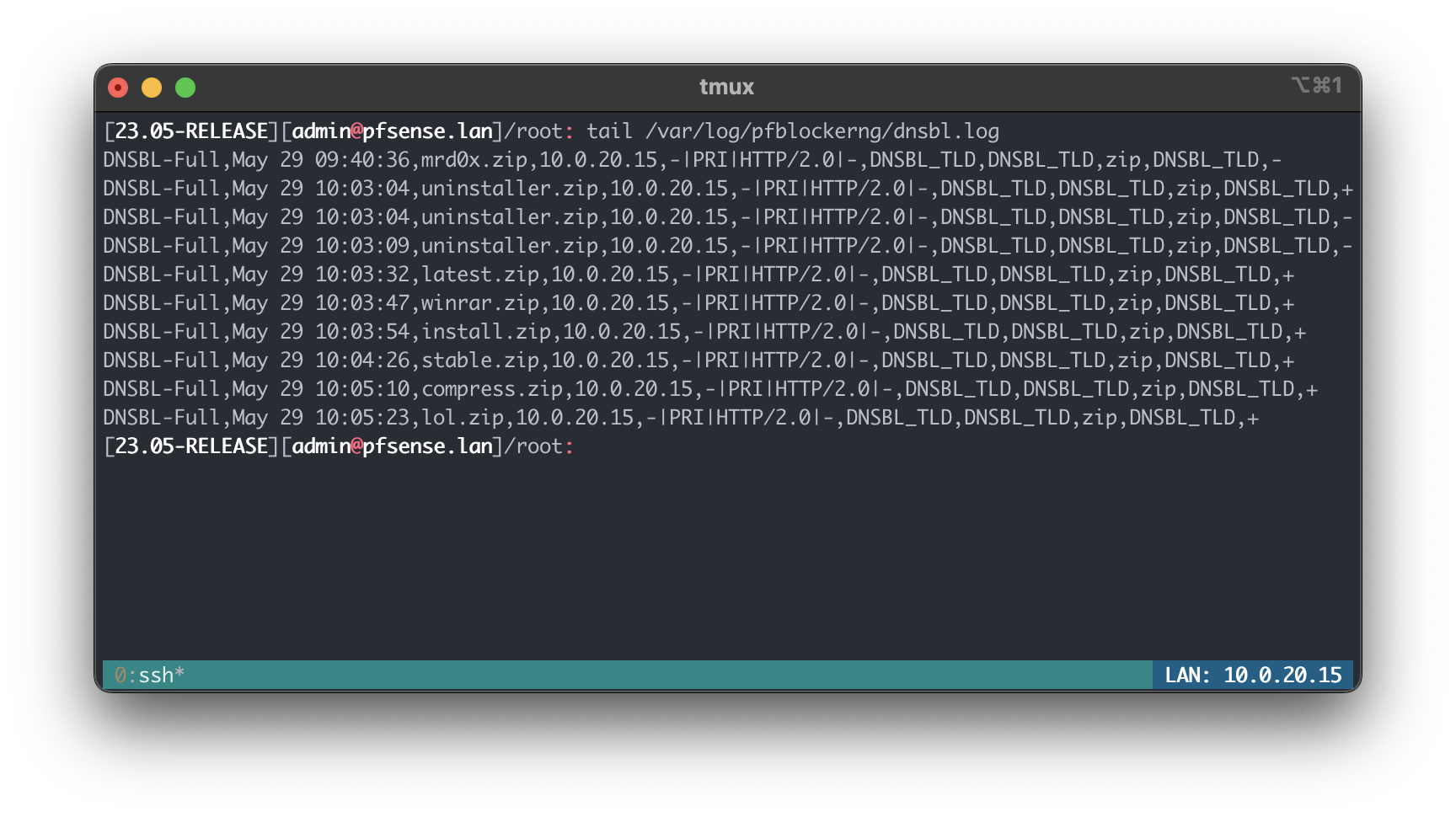
When any of the devices on my network try access a .zip domain, they’ll get an error. Or more specifically the domain will resolve to an internal address which shows a this site has been blocked message.
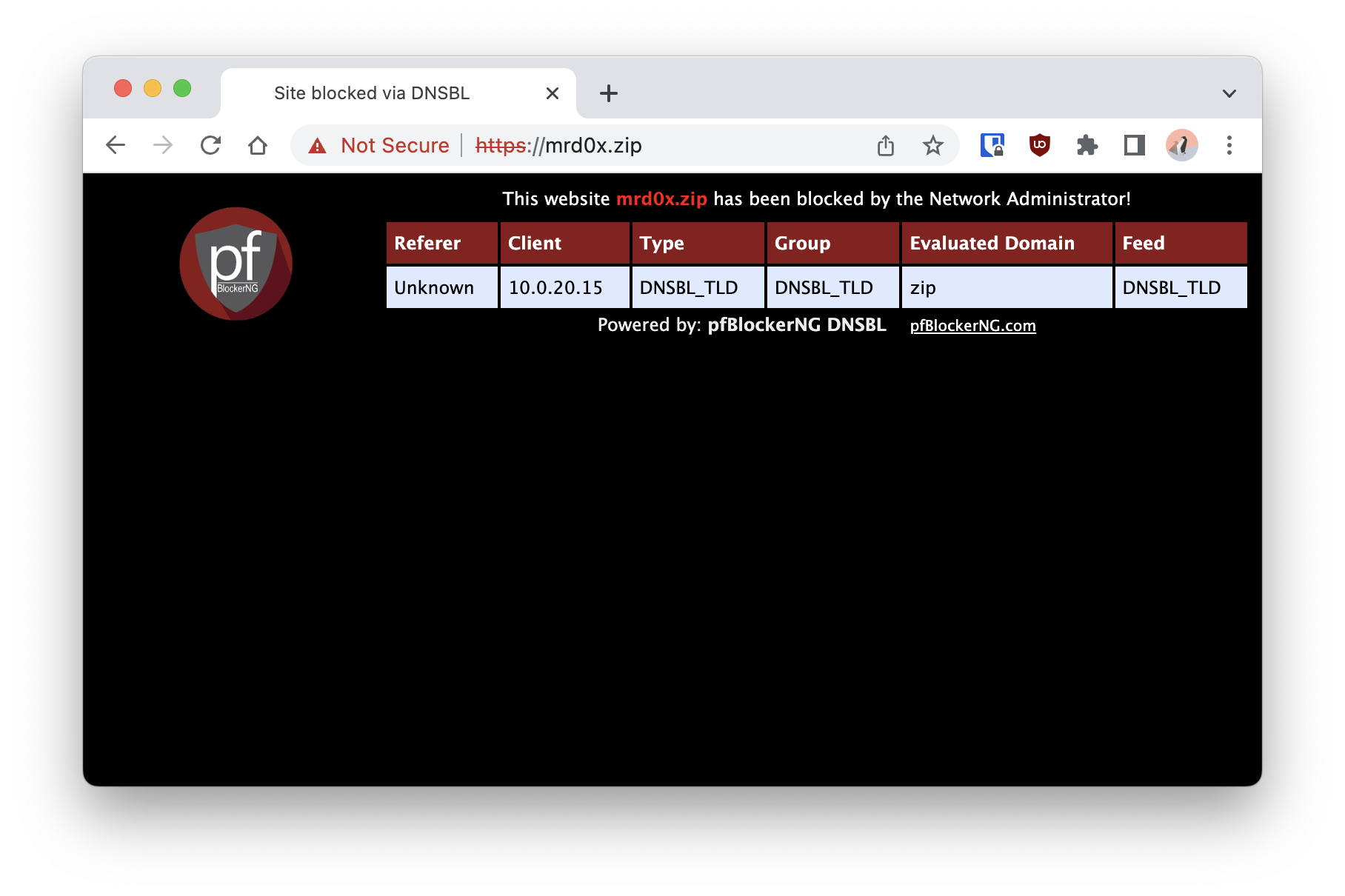
This page also can be customised by modifying dnsbl_active.php file located in:
/usr/local/www/pfblockerng/www/dnsbl_active.php
DNS lookup
pfBlockerNG was configured to use a IP range outside my VLAN. All the blocked domains will resolve to 10.10.10.1. Here’s an example of using the dig utility:
➜ ~ dig +short nic.zip
10.10.10.1
➜ ~ dig +short 124.zip
10.10.10.1
➜ ~ dig +short latest.zip
10.10.10.1
➜ ~ dig +short stable.zip
10.10.10.1
➜ ~ dig +short winrar.zip
10.10.10.1
Other misused TLDs
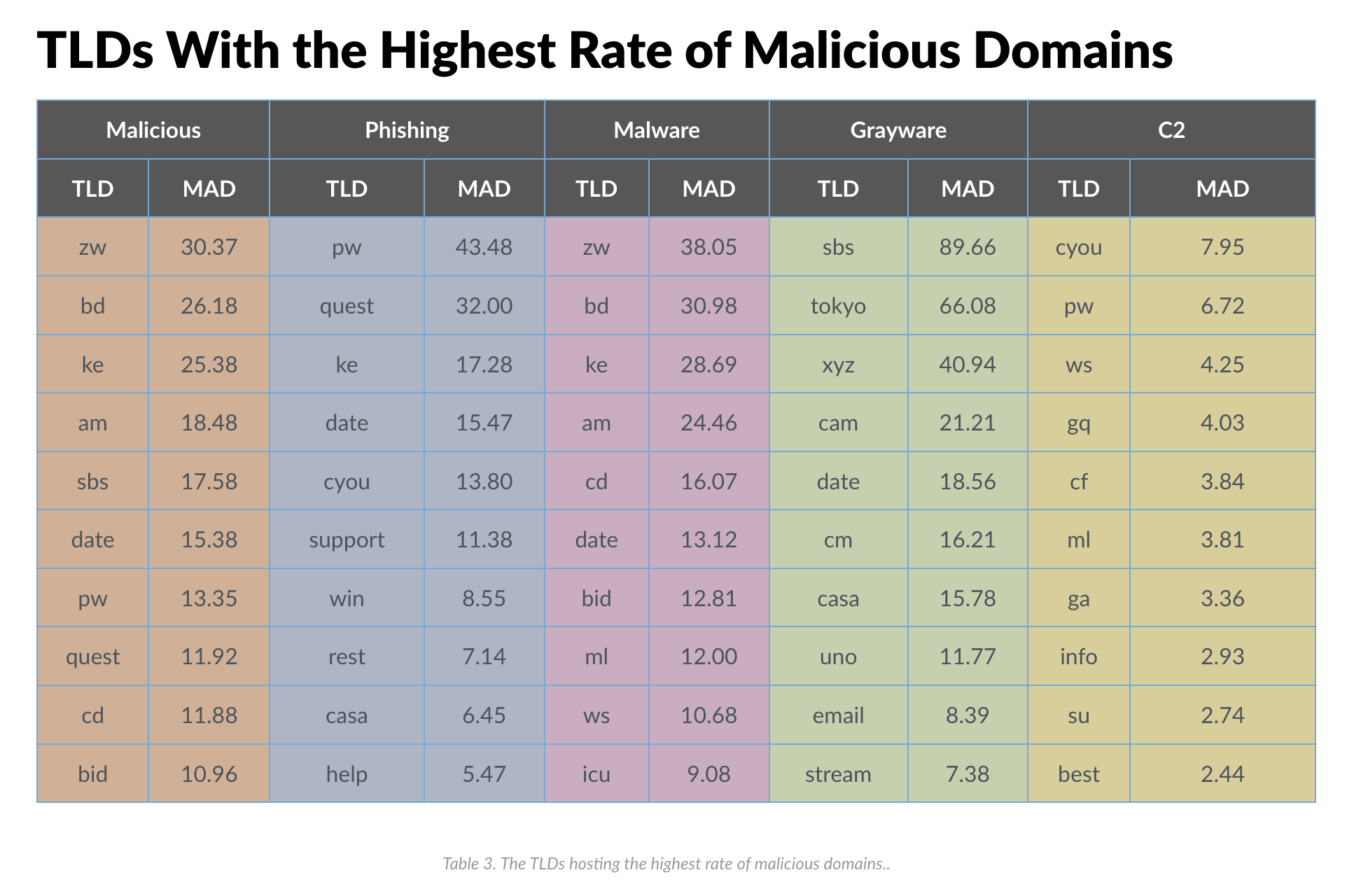
In 2021, Palo Alto’s Unit 42 threat intelligence team published a blog about their research of popular top-level domains used in cyber crime. The team looked at several different TLDs across six categories (Malicious, Phishing, Malware, Grayware, C2, and Sensitive).
A table from Palo Alto’s blog of TLDs with the highest number of malicious domains: